The most primitive DeFi attack vector and what you can do about it
With the advent of DeFi, ethereum users have witnessed a true 10x improvement to the legacy financial system. We are now able to earn roughly 10x the amount of interest we get on our bank accounts, are able to issue and use US dollars on ethereum without a US bank account and can openly audit the services themselves (good luck trying that with your bank).
While this is a great leap forward for the industry, we are still prone to the same old web 2.0 attack vectors of the past.
The mechanics of the recent DeFi Attack
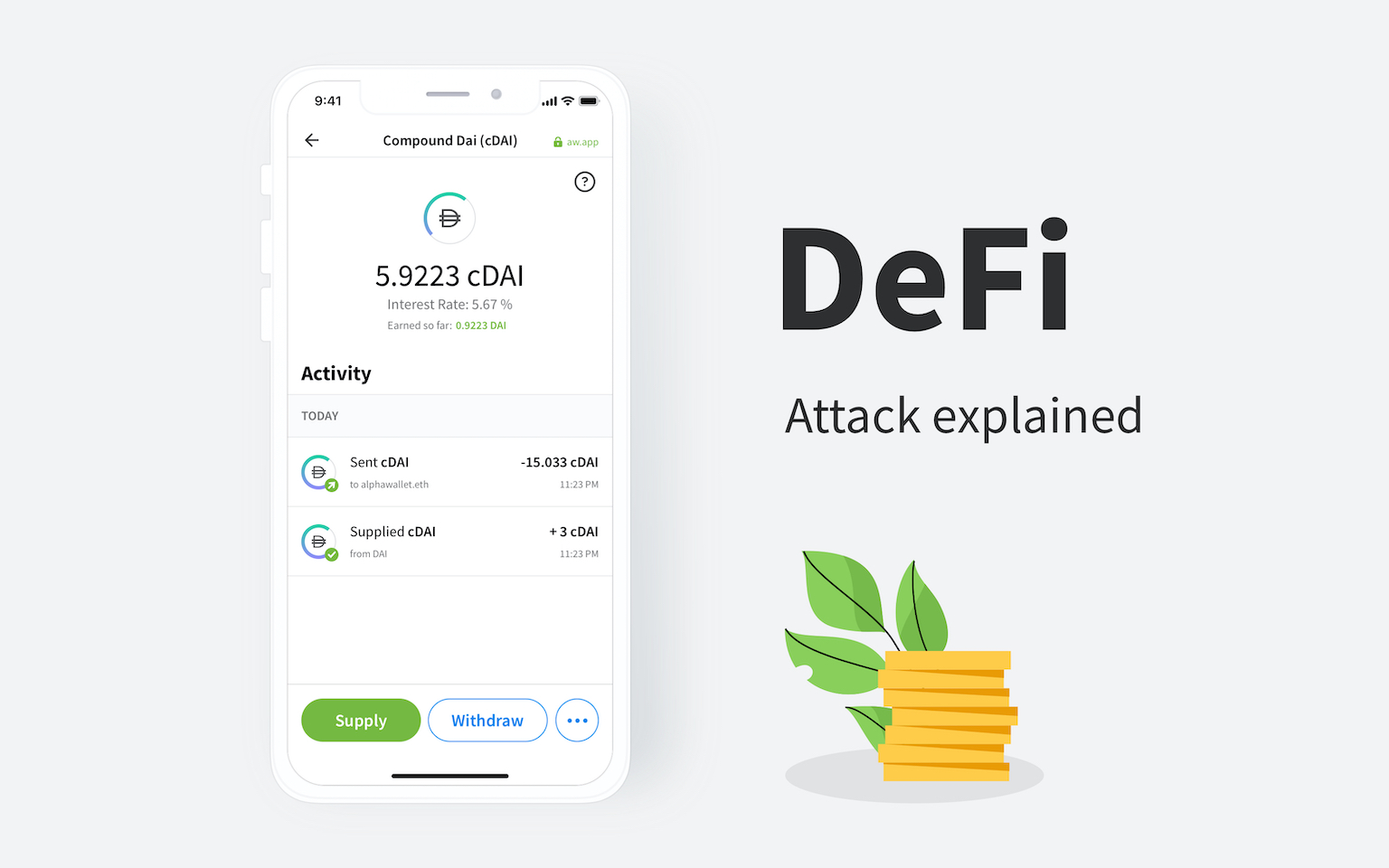
The attack vector I am talking about is not anything advanced like what was highlighted by Ameen’s awesome analysis on the compound protocol but something much more primitive: phishing.
In all the DeFi services that exist today, users must send an approval transaction to allow the DeFi contract to move funds on their behalf; for example, I approve the compound smart contract to move my DAI on my behalf when I want to lend or borrow from the platform.
Such a detail may seem trivial on the surface but it is not. It is super easy to fork the compound website and replace the contract with a malicious one, while running the site on a domain that looks very similar to the original.
The typical user will access such a service and send an approval transaction, only to find that you have not approved the legitimate compound contract but a malicious one which immediately confiscates all the DAI you have in your account.
Such a move is very easy to fall for as you are probably used to approving services like compound and won’t be bothered to actually verify what the contract does. This is the perfect opportunity for scammers to take advantage of both advanced and new users.

This poor fellow lost 14.1K worth of SAI by using a fake service
How AlphaWallet solves this problem
AlphaWallet is the first ethereum wallet to support TokenScript, an open source framework which allows you to write secure token logic modules and requires a signature from the author to provide assurance that it comes from a valid source.
TokenScript, once signed, cannot be tampered with or else the signature will become invalid and it will not run on your device without a warning.
Other token issuers can import your token logic and inherit the security, knowing it came from a valid author and is therefore free of malicious intent.
A TokenScript can be run on mobile with a native feel, meaning you will not have to write custom logic or a new app for iOS and Android to have your token working on mobile. TokenScripts can even be updated in real time without having to release a new app build.

Each user can see that the TokenScript is valid by checking the green tick and developers can verify the authenticity of the TokenScript modules they use by checking the signature manually
I am a token issuer, how can I get started with TokenScript?
Visit the TokenScript website and forum by clicking here or visit our GitHub here.
More on Blog